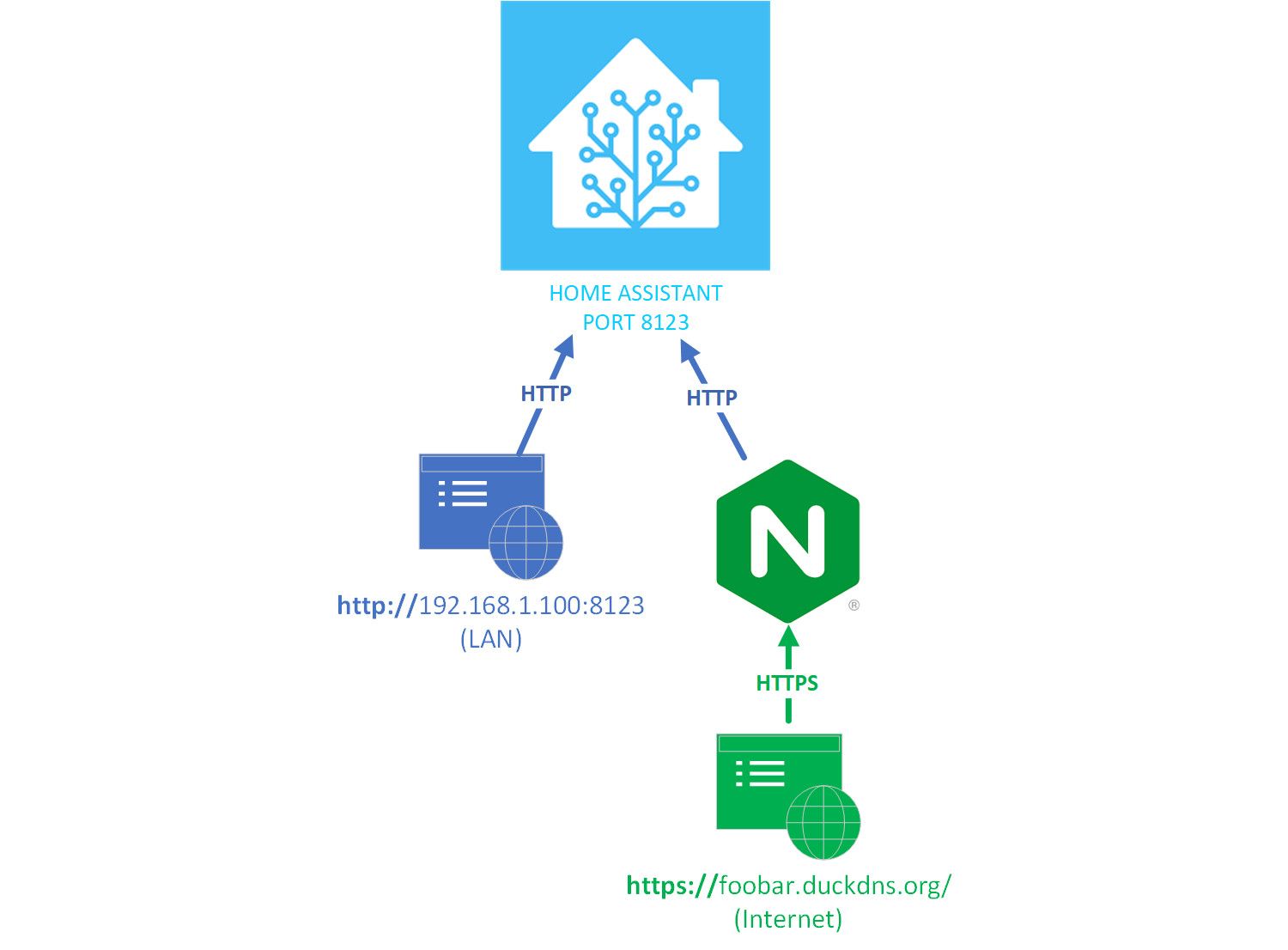
before #hass -v
root@raspberrypi:~# netstat -ntlp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 327/connmand
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 470/sshd: /usr/sbin
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 751/exim4
tcp 0 0 127.0.0.1:6010 0.0.0.0:* LISTEN 821/sshd: root@pts/
tcp 0 0 127.0.0.1:6011 0.0.0.0:* LISTEN 877/sshd: root@pts/
tcp 0 0 127.0.0.1:6012 0.0.0.0:* LISTEN 909/sshd: root@pts/
tcp6 0 0 ::1:53 :::* LISTEN 327/connmand
tcp6 0 0 :::22 :::* LISTEN 470/sshd: /usr/sbin
tcp6 0 0 ::1:25 :::* LISTEN 751/exim4
tcp6 0 0 ::1:6010 :::* LISTEN 821/sshd: root@pts/
tcp6 0 0 ::1:6011 :::* LISTEN 877/sshd: root@pts/
tcp6 0 0 ::1:6012 :::* LISTEN 909/sshd: root@pts/
tcp6 0 0 :::6600 :::* LISTEN 1/init
after #hass -v
root@raspberrypi:~# netstat -ntlp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 327/connmand
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 423/sshd: /usr/sbin
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 712/exim4
tcp 0 0 127.0.0.1:6010 0.0.0.0:* LISTEN 768/sshd: root@pts/
tcp 0 0 127.0.0.1:6011 0.0.0.0:* LISTEN 839/sshd: root@pts/
tcp 0 0 0.0.0.0:8123 0.0.0.0:* LISTEN 822/python3.9
tcp 0 0 127.0.0.1:6012 0.0.0.0:* LISTEN 881/sshd: root@pts/
tcp6 0 0 :::6600 :::* LISTEN 1/init
tcp6 0 0 ::1:53 :::* LISTEN 327/connmand
tcp6 0 0 :::22 :::* LISTEN 423/sshd: /usr/sbin
tcp6 0 0 ::1:25 :::* LISTEN 712/exim4
tcp6 0 0 ::1:6010 :::* LISTEN 768/sshd: root@pts/
tcp6 0 0 ::1:6011 :::* LISTEN 839/sshd: root@pts/
tcp6 0 0 :::8123 :::* LISTEN 822/python3.9
tcp6 0 0 ::1:6012 :::* LISTEN 881/sshd: root@pts/